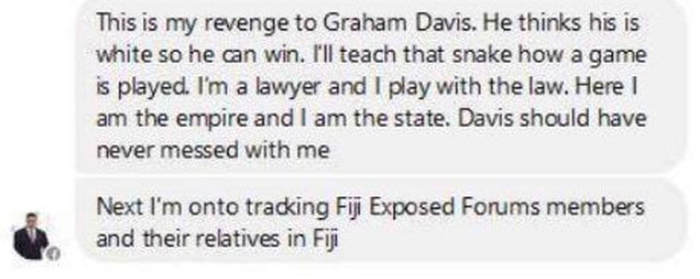
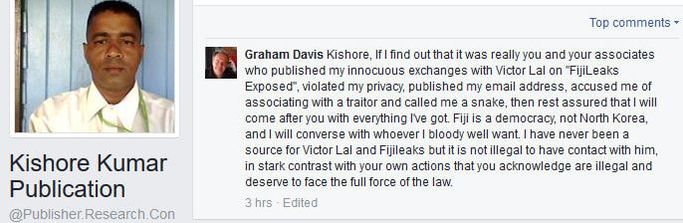
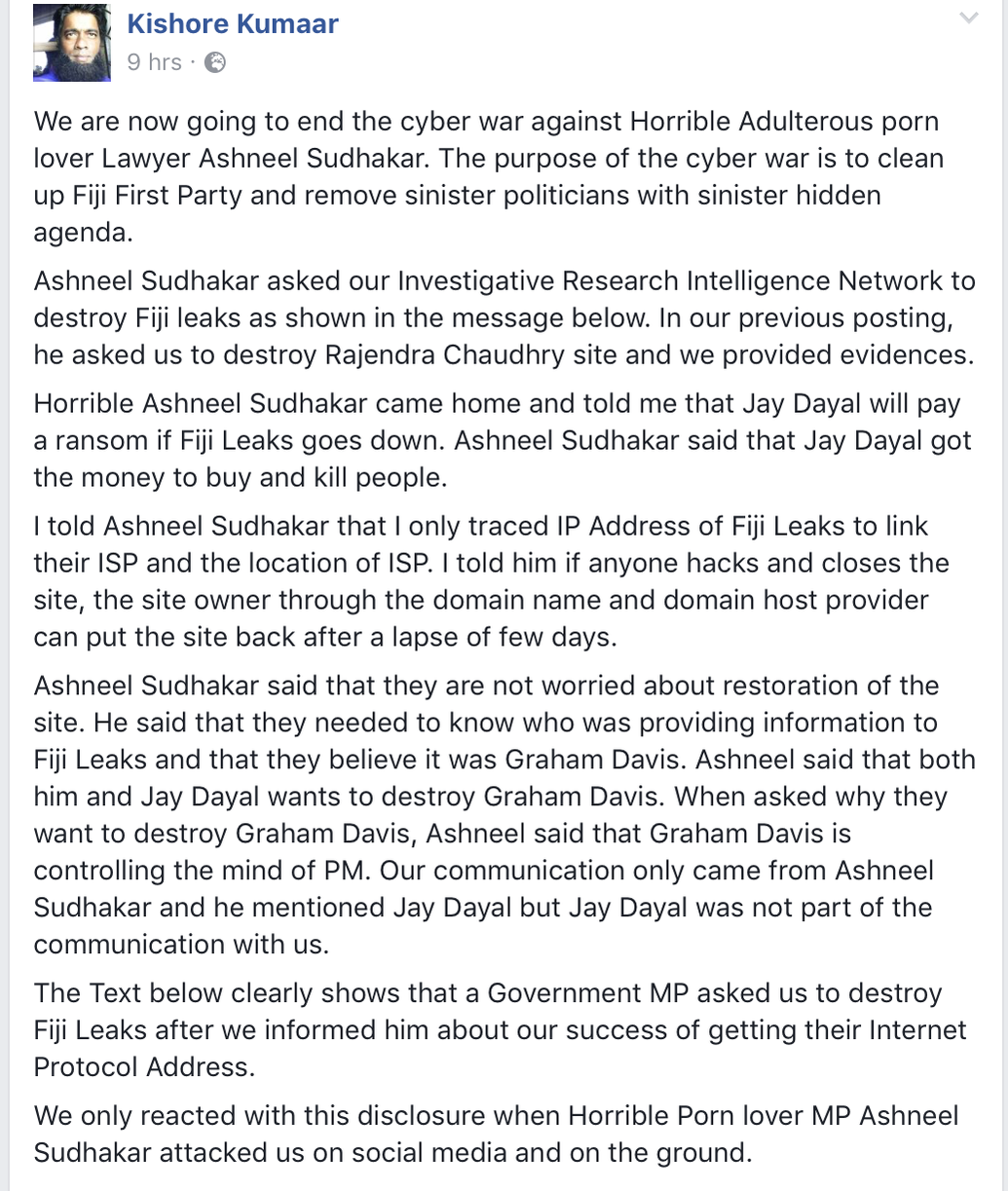
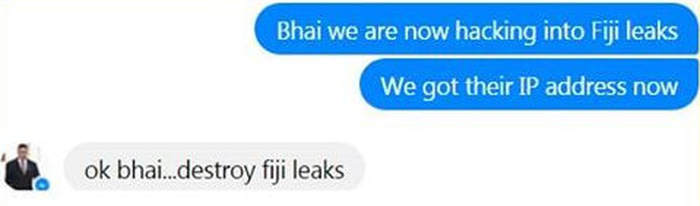
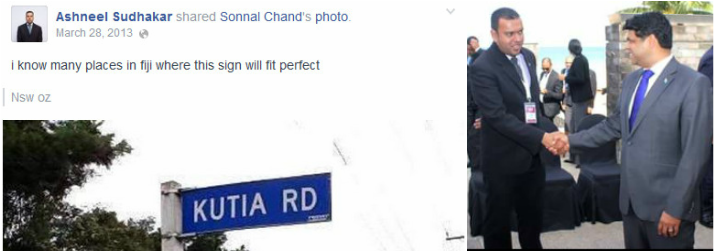
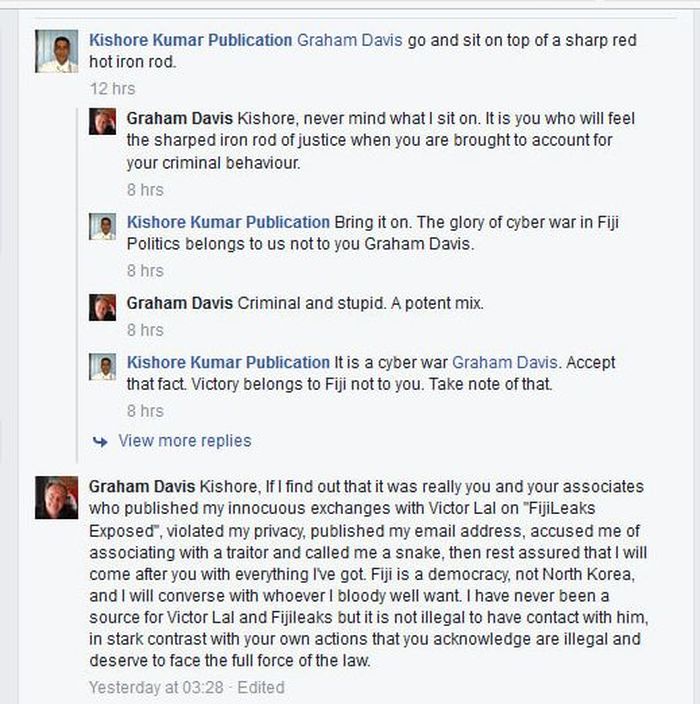
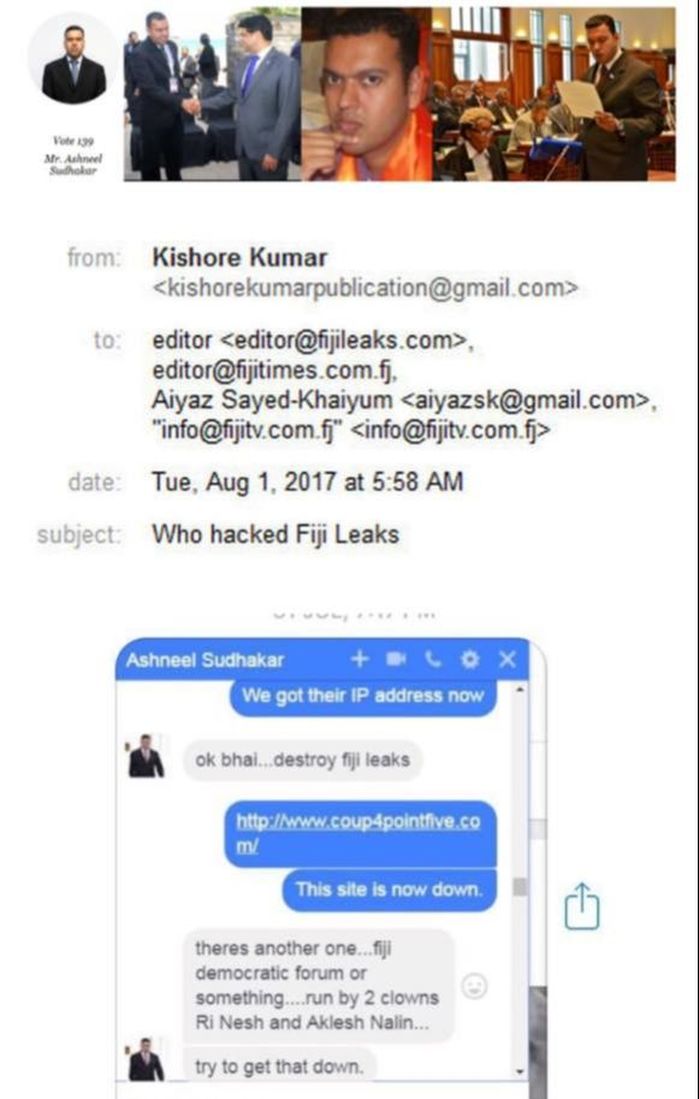
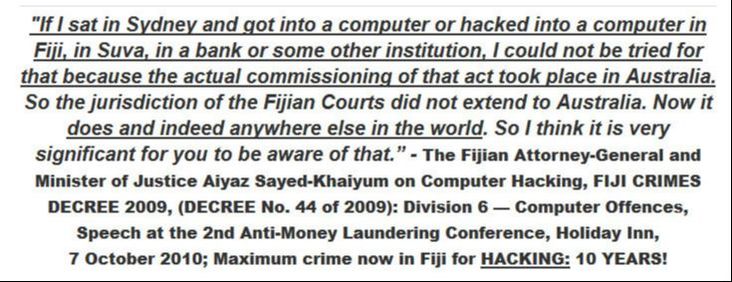
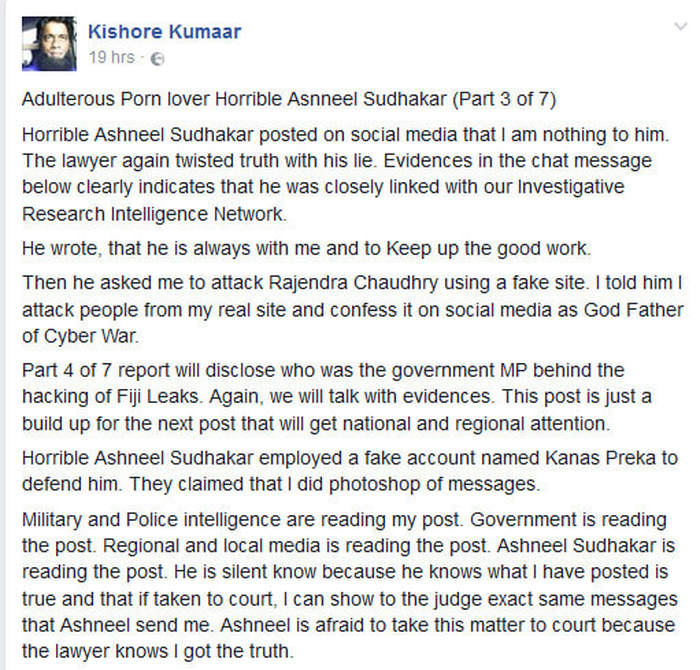
REEKING OF CRUDE RACISM: Kishore Kumar has also released the following explanation which he claims Ashneel Sudhakar provided to him
Now, Kishore Kumar has revealed more details on the hacking and who allegedly financed it, including the attack on Graham Davis, which borders on nothing but crude racism
Division 6 — Computer Offences
Definitions
336.—(1)
In this Division--
“access to data held in a computer” means--
(a)
the display of the data by the computer or any other output of the data from the computer; or
(b)
the copying or moving of the data to any other place in the computer or to a data storage device;
or
(c)
in the case of a program—the execution of the program.
“electronic communication” means a communication of information in any form by means of guided or unguided electromagnetic energy.
“impairment of electronic communication to or from a computer” includes--
(a)
the prevention of any such communication; or
(b)
the impairment of any such communication on an electronic link or network used by the
computer--
but does not include a mere interception of any such communication.
“modification”, in respect of data held in a computer, means -
(a)
the alteration or removal of the data; or
(b)
an addition to the data.
“unauthorised” access, modification or impairment has the meaning given in section 337.
(2)
In this Division, a reference to--
(a)
access to data held in a computer; or
(b)
modification of data held in a computer; or
(c)
the impairment of electronic communication to or from a computer--
is limited
to such access,
modification
or impairment
caused
(whether
directly
or indirectly)
by the
execution of a function of a computer.
Meaning of unauthorised access, modification or impairment
337.—(1) In this Division--
(a)
access to data held in a computer; or
(b)
modification of data held in a computer; or
1132
(c)
the impairment of electronic communication to or from a computer; or
(d)
the impairment of the reliability, security or operation of any data held on a computer disk, credit card
or other device used to store data by electronic means--
by
a person is unauthorised
if the person is not entitled
to cause that access,
modification
or
impairment.
(2)
Any such access, modification or impairment caused by the person
is not unauthorised
merely because he or she has an ulterior purpose for causing it.
(3) For the purposes
of an offence
under this Division,
a person causes any such unauthorised
access, modification
or impairment if the person’s conduct substantially contributes to it.
(4) for the purposes of sub-section (1), if--
(a)
a person
causes
any access,
modification
or impairment
of a kind mentioned
in that sub-section;
and
(b)
the person does so under a warrant issued under any law for the purpose of authorising such an
action--
the person is entitled to cause that access, modification or impairment.
Geographical jurisdiction
338.
A person commits an offence against all sections of this Division--
(a)
whether or not the conduct constituting the alleged offence occurs in fiji; and
(b)
whether or not a result of the conduct constituting the alleged offence occurs on fiji.
Saving of other laws
339.
This Division is not intended to exclude or limit the operation of any other law.
Serious computer offences
340.—(1)
A person commits an offence if he or she--
(a)
causes--
(i)
any unauthorised access to data held in a computer; or
(ii) any unauthorised modification of data held in a computer; or
(iii)
any unauthorised impairment of electronic communication to or from a computer; and
(b)
knows the access, modification or impairment is unauthorised; and
(c)
intends to commit, or facilitate the commission of, a serious offence against a law (whether by that
person or another person) by the access, modification or impairment.
(2)
In a prosecution for an offence against sub-section (1), it is not necessary to prove that the defendant knew
that the offence was--
(a)
an offence against a law; or
(b)
a serious offence.
(3)
A person who commits an offence against this section is punishable by a penalty not exceeding the penalty
applicable to the serious offence.
(4)
A person may be found guilty of an offence against this section even if committing the serious offence is
impossible.
(5)
It is not an offence to attempt to commit an offence against this section.
(6)
In this section--
“serious offence” means an offence that is punishable by imprisonment for life or a period of 5 or more
years.
1133
Unauthorised modification of data to cause impairment
341.—(1)
A person commits a summary offence if he or she--
(a)
causes any unauthorised modification of data held in a computer; and
(b)
knows the modification is unauthorised; and
(c)
is reckless as to whether the modification impairs or will impair--
(i)
access to that or any other data held in any computer; or
(ii)
the reliability, security or operation, of any such data.
Penalty — Imprisonment for 10 years.
(2)
A person may be guilty of an offence against this section even if there is or will be no actual impairment
to--
(a)
access to data held in a computer; or
(b)
the reliability, security or operation, of any such data.
(3)
A conviction for an offence against this section is an alternative verdict to a charge for an offence against
section 342 (unauthorised impairment of electronic communication).
Unauthorised impairment of electronic communication
342.—(1)
A person commits a summary offence if he or she--
(a)
causes any unauthorised impairment of electronic communication to or from a computer; and
(b)
knows that the impairment is unauthorised.
Penalty — Imprisonment for 10 years.
(2)
A conviction for an offence against this section is an alternative verdict to a charge for an offence against
section 341 (unauthorised modification of data to cause impairment).
Unauthorised access to, or modification of, restricted data
343.—(1)
A person commits a summary offence if he or she--
(a)
causes any unauthorised access to, or modification of, restricted data; and
(b)
intends to cause the access or modification; and
(c)
knows that the access or modification is unauthorised.
Penalty — Imprisonment for 2 years.
(2)
In this section--
“restricted data” means data--
(a)
held in a computer; and
(b)
to which access is restricted by an access control system associated with a function of the
computer.
Unauthorised impairment of data held on a computer disk, etc.
344.
A person commits a summary offence if he or she--
(a)
causes any unauthorised impairment of the reliability, security or operation of data held on--
(i)
a computer disk; or
(ii)
a credit card; or
(iii)
another device used to store data by electronic means; and
(b)
intends to cause the impairment; and
(c)
knows that the impairment is unauthorised.
Penalty — Imprisonment for 2 years.